Know Your Enemies


Understanding Hacker Types and How to Protect Yourself
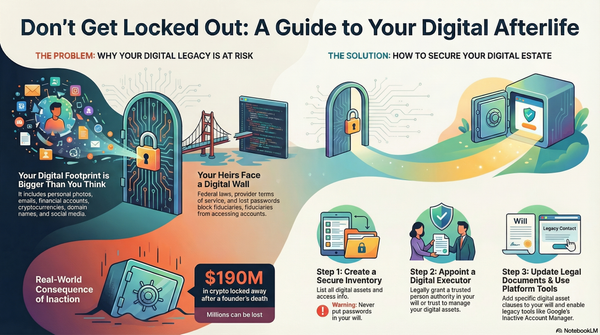
The digital landscape is filled with various threat actors, each with different motivations and methods. Understanding these different types of hackers and implementing appropriate security measures is crucial for both businesses and individual social media users. This article explores the main categories of hackers and provides practical protection strategies.
Types of Hackers
White Hat Hackers (Ethical Hackers)
White hat hackers are the cybersecurity professionals who work to identify and fix security vulnerabilities. They operate with permission and within legal boundaries, often employed by companies to conduct penetration testing and security audits. These hackers help strengthen digital defenses rather than exploit them.
Black Hat Hackers (Malicious Hackers)
Black hat hackers are the stereotypical "bad guys" of the cybersecurity world. They break into systems without permission, steal data, deploy malware, and cause damage for personal gain, revenge, or simply the thrill of causing chaos. Their activities are illegal and can result in significant financial and reputational damage to their targets.
Gray Hat Hackers
Gray hat hackers operate in the middle ground between ethical and malicious hacking. They may discover vulnerabilities without permission but then report them to the affected organization, sometimes requesting payment or recognition. While their intentions may not be entirely malicious, their methods still operate in legal gray areas.
Script Kiddies
Script kiddies are amateur hackers who use pre-written scripts and tools created by others to launch attacks. They typically lack deep technical knowledge and rely on automated tools to exploit known vulnerabilities. While less sophisticated, they can still cause significant damage through widespread, indiscriminate attacks.
Hacktivists
Hacktivists are politically or socially motivated hackers who target organizations, governments, or individuals to promote their ideological agenda. Groups like Anonymous fall into this category. Their attacks often aim to expose information, disrupt services, or make political statements rather than achieve financial gain.
State-Sponsored Hackers
These are highly sophisticated threat actors backed by nation-states. They typically target foreign governments, critical infrastructure, or companies with valuable intellectual property. State-sponsored hackers often have significant resources and advanced tools at their disposal, making them among the most dangerous threat actors.
Cybercriminals
Cybercriminals are motivated primarily by financial gain. They engage in activities like identity theft, credit card fraud, ransomware attacks, and cryptocurrency theft. These hackers often operate in organized groups and have turned cybercrime into a lucrative business model.
Protection Strategies for Businesses
Implement Multi-Layered Security
Businesses should adopt a defense-in-depth approach that includes firewalls, intrusion detection systems, antivirus software, and endpoint protection. No single security measure is foolproof, so multiple layers create redundancy and improve overall protection.
Regular Security Audits and Penetration Testing
Engaging white hat hackers to conduct regular security assessments helps identify vulnerabilities before malicious actors can exploit them. These tests should cover both technical infrastructure and human factors like social engineering susceptibility.
Employee Training and Awareness
Human error remains one of the biggest security vulnerabilities. Regular training programs should educate employees about phishing attacks, social engineering tactics, password security, and safe browsing practices. Simulated phishing exercises can help reinforce these lessons.
Access Control and Privilege Management
Implement the principle of least privilege, ensuring employees only have access to the systems and data necessary for their roles. Use multi-factor authentication for all critical systems and regularly review and update access permissions.
Data Encryption and Backup Strategies
Encrypt sensitive data both in transit and at rest. Maintain regular, tested backups stored in multiple locations, including offline storage to protect against ransomware attacks. Ensure backup systems are regularly tested and can be quickly restored.
Incident Response Planning
Develop and regularly test incident response plans that outline clear procedures for detecting, containing, and recovering from security breaches. This should include communication protocols, legal considerations, and stakeholder notification procedures.
Keep Systems Updated
Maintain current patches and updates for all software, operating systems, and security tools. Implement automated patch management systems where possible to ensure timely updates of critical security fixes.
Protection Strategies for Social Media Users
Strong Authentication Practices
Use unique, complex passwords for each social media account and enable two-factor authentication wherever possible. Password managers can help generate and store strong passwords securely.
Privacy Settings Management
Regularly review and adjust privacy settings on all social media platforms. Limit the amount of personal information visible to strangers and be cautious about location sharing features that could reveal your whereabouts.
Be Cautious with Links and Downloads
Avoid clicking on suspicious links or downloading files from unknown sources. Hackers often use social media to distribute malware or direct users to phishing websites designed to steal credentials.
Think Before You Share
Be mindful of the personal information you share on social media. Details like your full name, birthday, location, and personal relationships can be used by cybercriminals for identity theft or social engineering attacks.
Monitor Your Accounts
Regularly check your social media accounts for unauthorized activity, such as posts you didn't make or friend requests you didn't send. Enable notifications for login attempts from new devices or locations.
Use Secure Networks
Avoid accessing social media accounts over public Wi-Fi networks, which can be easily compromised. If you must use public Wi-Fi, consider using a VPN to encrypt your internet connection.
Verify Friend Requests and Messages
Be skeptical of friend requests from people you don't know personally, and verify the identity of people sending you messages, especially if they're asking for personal information or money.
Emerging Threats and Future Considerations
The cybersecurity landscape continues to evolve rapidly. Artificial intelligence is being used both by defenders to improve security systems and by attackers to create more sophisticated threats. Deepfakes and AI-generated content are making social engineering attacks more convincing, while the Internet of Things is expanding the attack surface for both businesses and individuals.
Staying informed about emerging threats and continuously updating security practices is essential. Consider subscribing to cybersecurity news sources and participating in security awareness training programs to stay current with the latest protection strategies.
Conclusion
Understanding the various types of hackers and their motivations is the first step in developing effective protection strategies. Whether you're a business owner securing corporate assets or an individual protecting your personal information on social media, implementing comprehensive security measures and maintaining vigilant awareness are crucial for staying safe in our increasingly connected world.
The key to effective cybersecurity lies in combining technical solutions with human awareness and maintaining a proactive rather than reactive approach to digital security. By understanding the threats and implementing appropriate protections, both businesses and individuals can significantly reduce their risk of becoming victims of cybercrime.