Defense in Depth
Defense in Depth: Building Layered Security for Business and Personal Protection
In medieval times, castles weren't protected by a single wall. They featured multiple barriers: moats, outer walls, inner walls, towers, and a final keep. Each layer served as a backup when the previous one failed. This same principle applies to modern cybersecurity through a strategy called Defense in Depth.
Defense in Depth is a cybersecurity approach that uses multiple layers of security controls to protect information and systems. Rather than relying on a single security measure, this strategy creates overlapping defenses that work together to detect, prevent, and respond to cyber threats.
Why Single-Point Security Fails
Many organizations and individuals make the mistake of treating cybersecurity like a single lock on a door. They install antivirus software or use strong passwords and assume they're protected. However, cybercriminals are persistent and creative. If they can bypass your one security measure, they have complete access to your digital assets.
Recent data breaches at major corporations demonstrate this vulnerability. Companies that relied heavily on perimeter security found themselves helpless once attackers gained initial access to their networks.
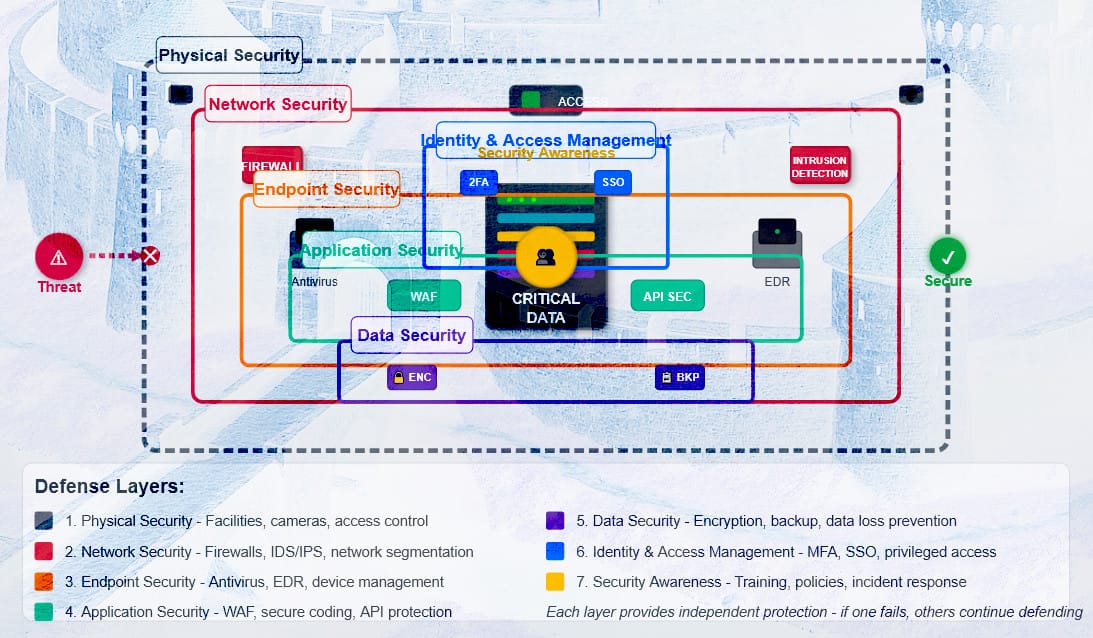
The Defense in Depth Model: Seven Essential Layers
Effective cybersecurity requires protection at multiple levels, each serving a specific purpose in your overall security strategy.
Layer 1: Physical Security
For Businesses: Secure server rooms, require badge access, install security cameras, and implement visitor management systems. Ensure that sensitive equipment cannot be accessed by unauthorized personnel.
For Personal Users: Protect your devices physically. Don't leave laptops unattended in public spaces, use privacy screens when working in open areas, and secure your home router in a locked cabinet if possible.
Layer 2: Network Security
For Businesses: Deploy firewalls, implement network segmentation, use intrusion detection systems, and regularly monitor network traffic for suspicious activity. Consider implementing a zero-trust network architecture.
For Personal Users: Change default router passwords, enable WPA3 encryption on your home Wi-Fi, disable WPS, and consider using a guest network for visitors and IoT devices.
Layer 3: Endpoint Security
For Businesses: Install enterprise-grade antivirus software, enable automatic updates, implement endpoint detection and response (EDR) solutions, and enforce device encryption policies.
For Personal Users: Keep operating systems and software updated automatically, use reputable antivirus software, enable device encryption, and install apps only from official stores.
Layer 4: Application Security
For Businesses: Conduct regular security assessments of custom applications, implement secure coding practices, use web application firewalls, and maintain an inventory of all software assets.
For Personal Users: Review app permissions regularly, uninstall unused applications, keep all apps updated, and be cautious about granting excessive permissions to mobile apps.
Layer 5: Data Security
For Businesses: Classify data based on sensitivity, implement encryption for data at rest and in transit, establish data loss prevention (DLP) policies, and maintain secure backup systems.
For Personal Users: Use cloud storage with strong encryption, regularly back up important files to multiple locations, encrypt sensitive documents, and be mindful of what personal information you share online.
Layer 6: Identity and Access Management
For Businesses: Implement multi-factor authentication (MFA) for all systems, follow the principle of least privilege, conduct regular access reviews, and use single sign-on (SSO) solutions where appropriate.
For Personal Users: Enable two-factor authentication on all important accounts, use unique passwords for each account, consider using a password manager, and regularly review and revoke access to third-party applications.
Layer 7: Security Awareness and Training
For Businesses: Conduct regular cybersecurity training sessions, perform phishing simulations, establish clear security policies, and create incident response procedures.
For Personal Users: Stay informed about current threats, be skeptical of unsolicited messages, verify requests for sensitive information through alternative channels, and learn to recognize phishing attempts.
Protecting Your Social Media Accounts: A Defense in Depth Approach
Social media platforms are prime targets for cybercriminals because they contain vast amounts of personal information and serve as gateways to other accounts and relationships.
Immediate Actions You Can Take Today
Enable Two-Factor Authentication: This single step dramatically reduces your risk of account compromise. Use authenticator apps rather than SMS when possible, as text messages can be intercepted.
Review Privacy Settings: Limit who can see your posts, personal information, and friend lists. Many platforms default to overly permissive settings that expose more information than necessary.
Audit Connected Applications: Review and remove third-party apps that no longer need access to your accounts. These applications often request broad permissions that could be exploited.
Use Strong, Unique Passwords: Each social media account should have its own complex password. Password managers make this manageable by generating and storing unique passwords for each account.
Advanced Social Media Security Measures
Monitor Login Activity: Most platforms show you where and when your account was accessed. Review this information regularly and report suspicious activity immediately.
Limit Personal Information Sharing: Avoid posting information that could be used for identity theft or social engineering, such as full birth dates, phone numbers, or location check-ins in real-time.
Be Cautious with Friend Requests: Cybercriminals often create fake profiles to gather information or distribute malware. Verify the identity of new connections through alternative channels.
Use Platform-Specific Security Features: Many social media platforms offer advanced security options like login alerts, device management, and trusted contacts for account recovery.
Implementation Strategy: Start Small, Build Systematically
For Business Owners
Begin with the most critical layers: ensure all devices have updated antivirus software, implement multi-factor authentication for business accounts, and conduct basic employee training. Gradually add more sophisticated protections like network monitoring and endpoint detection systems.
Consider working with a cybersecurity consultant to assess your current posture and prioritize improvements based on your specific risks and budget constraints.
For Individual Users
Start with the basics: enable two-factor authentication, use a password manager, and update your devices regularly. Once these habits are established, move on to more advanced measures like network security and privacy settings optimization.
Common Mistakes to Avoid
Over-Reliance on Technology: Security tools are important, but human behavior remains the weakest link. No amount of technology can protect against poor decision-making.
Neglecting Updates: Outdated software represents one of the most common attack vectors. Automatic updates should be enabled whenever possible.
Assuming Compliance Equals Security: Meeting regulatory requirements is important, but it represents a minimum baseline, not comprehensive protection.
Ignoring Insider Threats: Not all security breaches come from external attackers. Implement controls that protect against both malicious and accidental insider actions.
The Continuous Nature of Cybersecurity
Defense in Depth is not a one-time implementation but an ongoing process. Cyber threats constantly evolve, requiring regular assessment and adjustment of your security measures. Schedule monthly reviews of your security posture, stay informed about emerging threats, and be prepared to adapt your defenses as new vulnerabilities are discovered.
Remember that cybersecurity is ultimately about risk management, not risk elimination. The goal is to make yourself or your organization a harder target than the alternatives, causing attackers to move on to easier prey.
Taking Action
Cybersecurity can feel overwhelming, but Defense in Depth provides a clear framework for systematic protection. Start with the layer that represents your greatest vulnerability, implement basic protections, and gradually build more comprehensive defenses.
Whether you're protecting a business or your personal digital life, the principles remain the same: multiple layers of security, regular monitoring and updates, and a commitment to continuous improvement. The time and effort invested in building robust defenses today will pay dividends in preventing costly breaches tomorrow.